
Anyone who owns a website needs to think of the data privacy concerns that their users may have when accessing the site. Of course, data privacy is more important in some organizations than others – banks have to place this concern at the top of the list – but it matters for every business. To treat your visitors and customers properly, and to fall within the scope of the law, you need to do this right.
Unfortunately, this is an area that can feel a little overwhelming, especially if you aren’t particularly tech-savvy. Where do you even start? What are the risks, and how do you protect against hacking and other attempts to steal personal data? It’s a big topic, but you don’t need to become an expert to make some meaningful process. Let’s take a closer look in the article below so you can get on the right track.
Why This Matters
It’s relatively common for businesses to take data privacy for granted. Whether it’s because they don’t understand the size of the threat, or they just don’t think that working on data privacy is worth the cost, this is a mistake that can come back to haunt a business in a big way.
First and foremost, data privacy is important because it is part of offering good customer service. You certainly take seriously the task of serving your customers well in other areas – like offering support on your goods and services, or charging fair prices – and you should take data privacy seriously, as well. These customers are trusting your organization with their personal information and violating that trust will likely mean that they are never coming back.
Beyond doing right by your customers, there is also the matter of organizational costs to consider. If you think that it costs too much to tend to data privacy concerns, you should compare those expenses with what you will have to spend after a breach. The average cost of breached customer data has soared into the millions, and that doesn’t even consider what you might have to pay in lawsuits down the line. It’s also hard to quantify the impact of a breach on the reputation of your company and how willing customers are to do business with you moving forward. When you add it all up, it becomes painfully clear that data privacy is simply a topic that no business can afford to ignore.
Knowing the Threats

With the seriousness of this topic made clear, let’s start to talk about what kinds of threats exist that could expose your customer data. How will bad actors gain access to the data? Tactics and techniques are always shifting, but the list below highlights some of the common threats that can do harm to businesses of all sizes.
- Insiders. Believe it or not, one of the biggest threats to the security of the customer data that you store can come from inside the company. While it’s easy enough to naturally trust everyone you employ or work with, there is a chance that someone will have bad intentions. Given the access that these people will have to your system, it’s relatively easy to do significant damage without being detected. For that reason, having some form of checks and balances in place to make sure a single employee doesn’t have unrestricted access to everything you store is a good place to start.
- Phishing. Most people have heard of this type of attack, yet it continues to work because expert criminals can disguise their phishing messages so effectively. The idea here is to send an email to people in the company that looks like an authentic message from someone that would normally send them an email – a vendor or some type of service provider. If the recipient clicks on the link in the email and takes the requested action, it can result in the system being made vulnerable to an attack. Consistent education throughout your organization about the threat of phishing and how to steer clear of trouble can help limit the likelihood of problems with this form of cybercrime.
- Ransomware. The name of this type of attack pretty much says it all. In this case, the attacker is going to break into your device or network and lock it down using malware. Then, the company or an individual will be contacted with a demand for payment. Only when that payment is made will the malware be lifted and the company can access its data once again. As you might imagine, the payment demands are extreme, and it can be nearly impossible for companies to get out of this type of situation without major losses.
These aren’t the only types of cyberattacks that can threaten data security in your business, but they are among the most popular. It pays to keep up with the latest trends in this area so you aren’t caught off guard by a new hacking strategy that you don’t notice until it is too late.
Start with the Basics
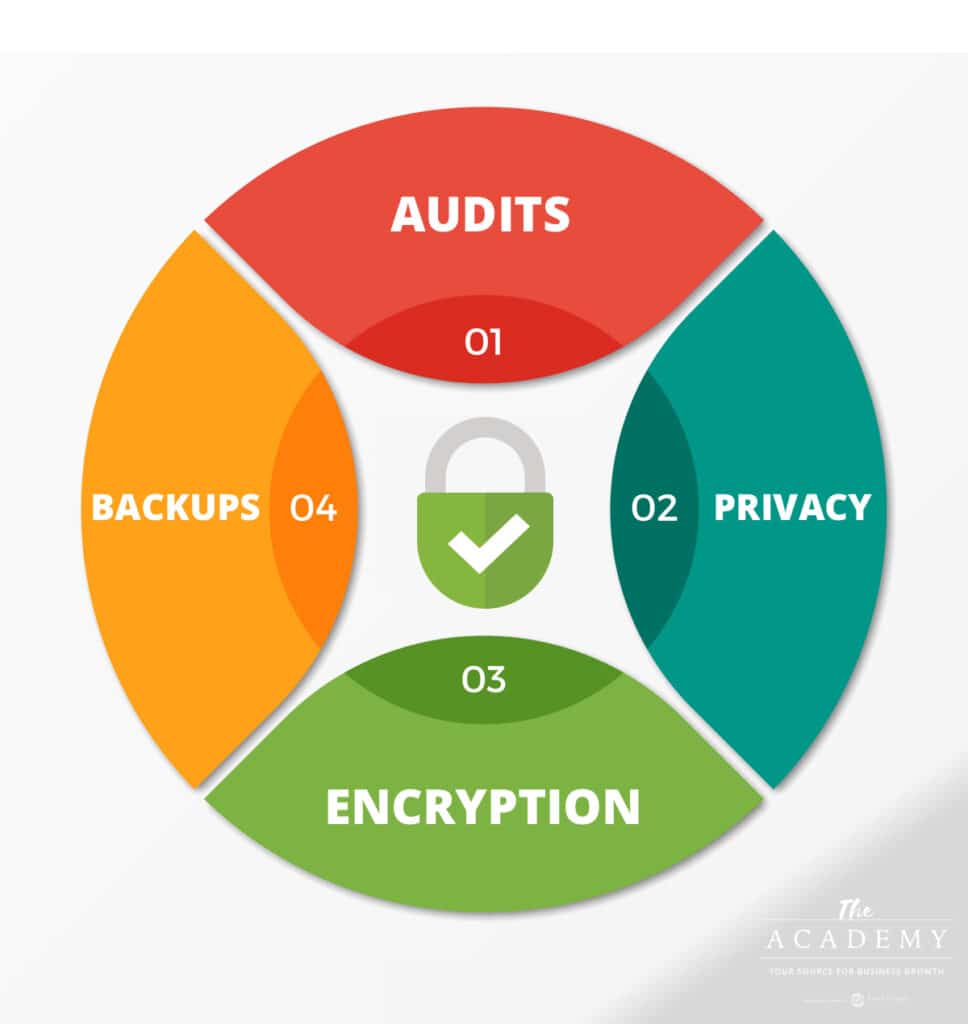
At this point, it’s time to get down to the fundamentals of data security in your organization. While it might seem like all doom-and-gloom on this topic, there is one bit of good news that we should point out – taking even basic steps can dramatically reduce your chances of becoming a victim.
Cybercriminals are typically going to take the path of least resistance, looking for easy ways to make money from companies that haven’t even handled the simple security measures. So, if you can make sure the fundamentals are in place to protect your data, any criminal who comes across your site might just decide to move on to an easier target. Get started by taking the following steps –
- Audit your collected data. You can’t properly protect data until you know exactly what it is that you are protecting. What data is collected by your organization and where is it stored? If you can’t easily answer this question, it’s time to take a closer look. It might be that you are collecting more data than is necessary, and you can cut back on what you gather to reduce your exposure to a security breach. Having minimal data won’t stop a breach from occurring, but it will reduce the damage and hopefully mean the incident is less costly if it does happen.
- Create a privacy policy. For the data that you do collect, create and publish a privacy policy that outlines how the data will be handled and what rights the customer has over how that data is used. If you have a legal team in your business, you’ll likely want to get them involved in the creation of a privacy policy so you can ensure that everything is handled correctly and the final language covers all of your bases.
- Ongoing backups. Taking regular backups of your entire system, and storing those backups in a secure location outside of your local network, is a big step in the right direction on data security. Specifically, this will help in a ransomware case, as you’ll have another version of your data saved and ready to go. Then, if someone does take over your site and demand money, you won’t have any reason to comply – you can just restore the system from one of the recent backups and very little will be lost.
- Always use encryption. It’s easier now than ever before to encrypt data that you store, so there is no excuse to skip this important step. When data is encrypted, it takes far more time and effort for a hacker to attempt to break through that layer of encryption to get at the raw data. Again, this is a matter of putting up as many roadblocks and obstacles as possible. Encryption is another layer that will give a criminal trouble and it may prove to be the piece that turns a potential breach into a non-event.
Additional Important Steps
If you take the time and minimal effort to handle the points above, you’ll already be on the right track. There is more that you can do, however, so continuing on to implement further strategies will make your data even safer and a costly even less likely to take place.
- Establish spam filters. Even with ongoing education, you can’t control the actions of your employees, and someone might make a mistake and click on something in a phishing email that exposes your entire system. To cut down on the chances of such an error, take the time to build spam filters in your organization to catch as many of those phishing messages as possible before they land in inboxes. Over time, you can add to these spam filters and continue to cut down on the threats you face.
- Limited access. This is a point that gets back to the topic of an insider being responsible for a breach. Take the time to build access roles for various people in the company as it relates to your network and your data. Then, only give each individual access to what they need to have in order to do their job successfully. If given more access than is needed, you are opening your business up unnecessarily to additional risk. When someone changes roles in the organization – say, they get a promotion – you can review their system access to see if they need to be given more freedom to view various forms of data.
- Multi-factor authentication. One of the best ways to keep your system secure is to use more than one form of authentication when a person logs in. For example, a single point of authentication is a password, so a system that is set up to require a password only is relatively easy to breach. However, if entering the password takes the user to a new screen where a code must be supplied that was sent to their phone, that takes the security level up significantly. Now, a criminal would need to find a way around that extra layer of authentication, which is much harder to do.
No system that is designed to protect data will be perfect. There are always vulnerabilities somewhere, and the tactics used by criminals to seek personal data that can be used for financial gain are always changing. We hope the tips above give you some direction as you aim to improve the security of your site and the data that it collects. Good luck!
Most Popular Articles

Seeing Favicons in Your Google Search Results? Here’s Why…
Have you noticed anything different in your Google Search results lately? Google added tiny favicon icons to its organic search results in January. It was…

Business Growth and Digital Marketing News & Tips 11-17-24
Are you encouraging and rewarding innovation? Lee Cockerell is the former Executive Vice President of Operations at Walt Disney World. A lover of traditional red…

Business Growth and Digital Marketing News & Tips 11-27-24
A culture of gratitude "Feeling gratitude and not expressing it is like wrapping a present and not giving it." – William Arthur Ward Beyond being…








